Azure Onboard Automator
08 Sep 2023
Introduction
I have so far completed two associate-level Azure certifications, primarily relying on Microsoft-provided labs with step-by-step instructions. However, to further enhance my hands-on experience, it is time to do more personal projects instead of practing for more certifications. This project takes inspiration from madebygps’ suggestions, which can be found on her GitHub repository here: https://github.com/madebygps/projects/tree/main/az-104
The objective of this project is to automate the onboarding process for new employees into Azure Active Directory (now known as Microsoft Entra ID) using Azure Logic Apps.
Services used
Azure Active Directory
Azure Active Directory (Azure AD) is a cloud-based solution for managing user identities, authentication, and resource access within an organization.
Azure Logic Apps
Azure Logic Apps is a cloud-based service provided by Microsoft that allows you to design and automate workflows that integrate various services. It uses pre-built or custom connectors that calls the service’s API. Triggers activates the workflow based on some event, while actions is an operation that performs a task in the workflow.
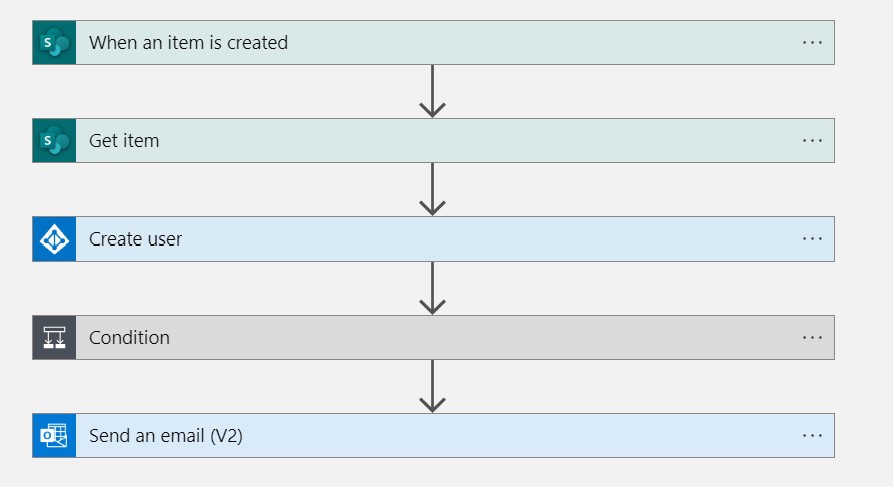
Onboarding workflow
Designing the Logic App
I initiated the project by creating a new Logic App in the Azure Portal and selecting the consumption plan. Once the Logic App was created, I entered the Logic App designer interface, where I could choose from common triggers or templates. I opted for a blank Logic App, which required a trigger to initiate the workflow. Two suggested triggers from the project page were an entry in a SharePoint list or an email sent to a specific mailbox.
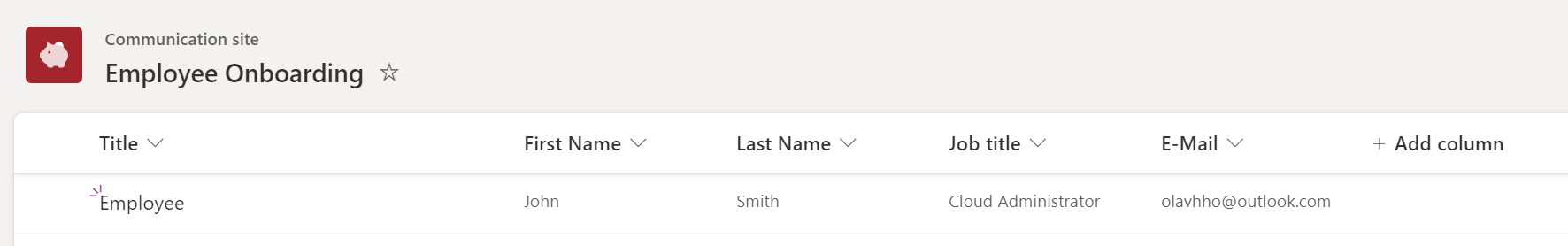
I had access to a SharePoint site through my Microsoft 365 Developer subscription, so I chose the SharePoint Connector and the trigger “When an item is created.” To facilitate this, I created a SharePoint list with the following columns:
I used the “Get item” action to retrieve information from the SharePoint list. This data was then utilized in the Azure AD connector to create a user:
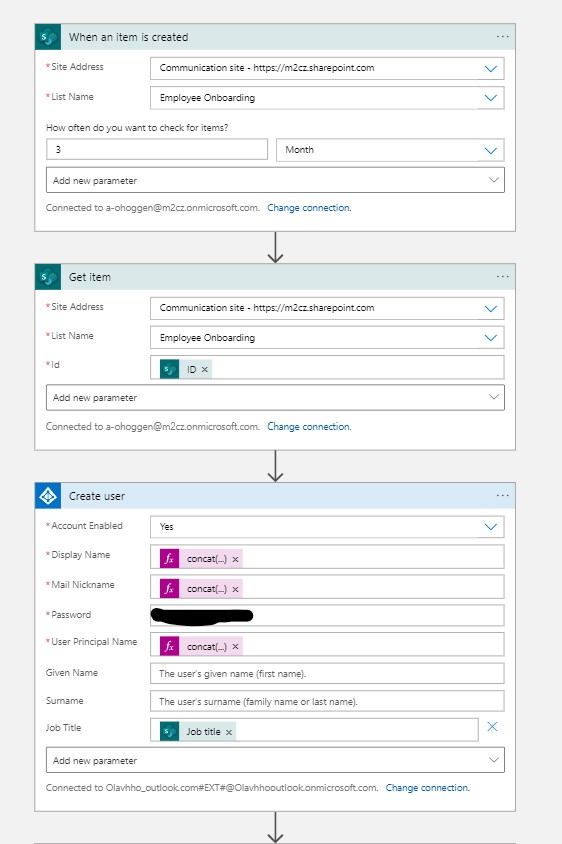
For instance, I retrieved the Display Name parameter using an Azure Expression like this: concat(body(‘Get_item’)?[‘FirstName’], ‘ ‘, body(‘Get_item’)?[‘LastName’]).
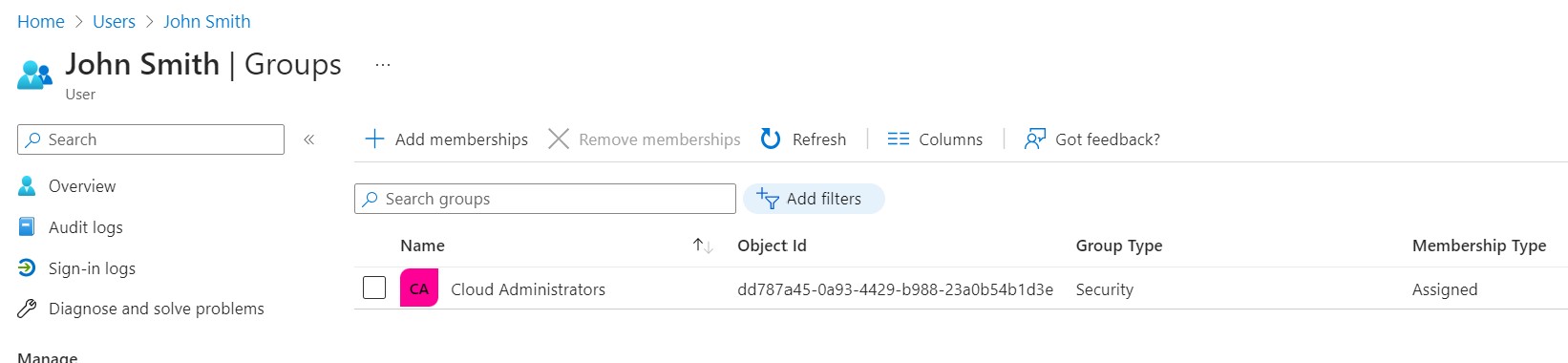
To determine how the user would gain access to Azure resources, I implemented a simple conditional statement based on the job title attribute. Although not highly scalable, it served the purpose for this prototype. In this example, if the job title is “Cloud Administrator,” the user is added to the “Cloud Administrators” group, which has contributor permissions to the 2023-09-08-OnboardAutomator resource group I am working in. An alternative option I explored was using dynamic assignment directly within the Azure group, but it required Azure AD Premium 1, which I didn’t have access to in the free version of Azure AD.
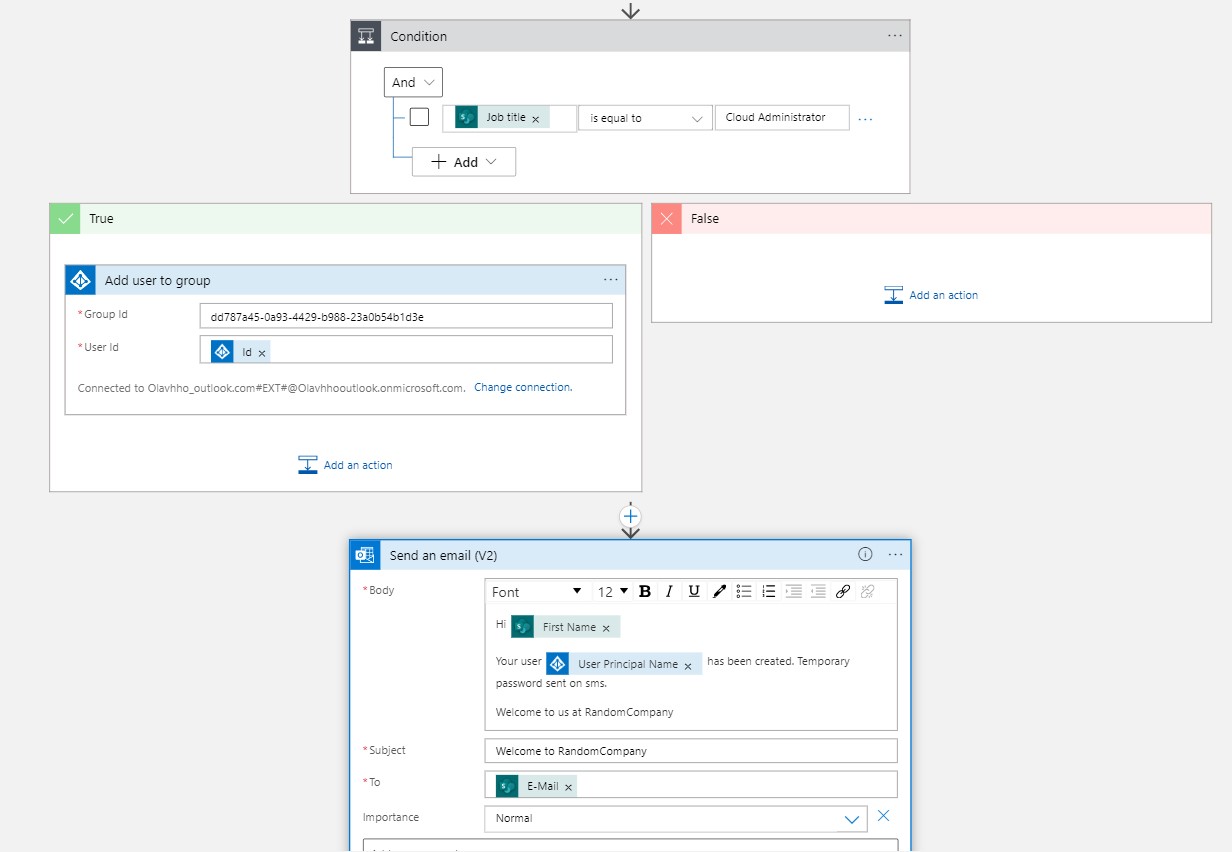
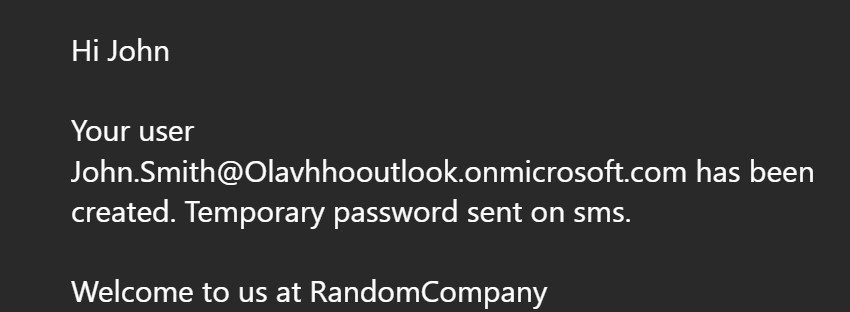
Last step was using the Outlook connector to send an email to the newly created user.
After configuring the steps in the Logic App designer you can trigger a run to check if it is working. As you can see not all my runs were successful and I had to do some troubleshooting to get it to work correctly.
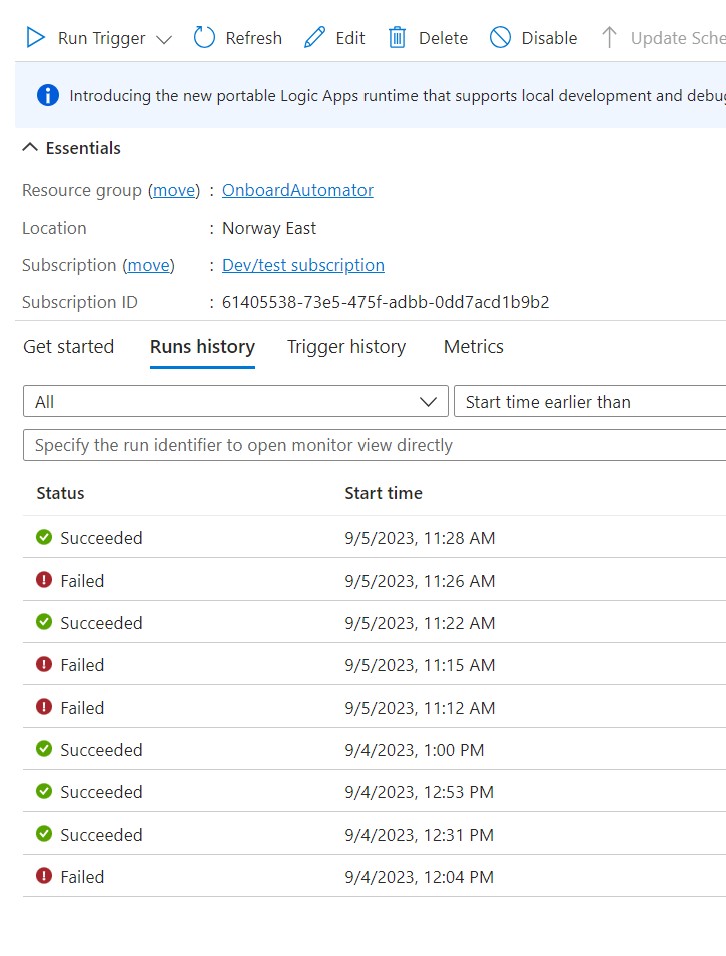
The errors were primarily related to typos in variables within the “Create user” action. Additionally, I discovered that I needed to create a new user each time the Logic App triggered. I did also try some different triggers other than the sharepoint item that did not intially work, before deciding on a sharepoint item as the simplest solution.
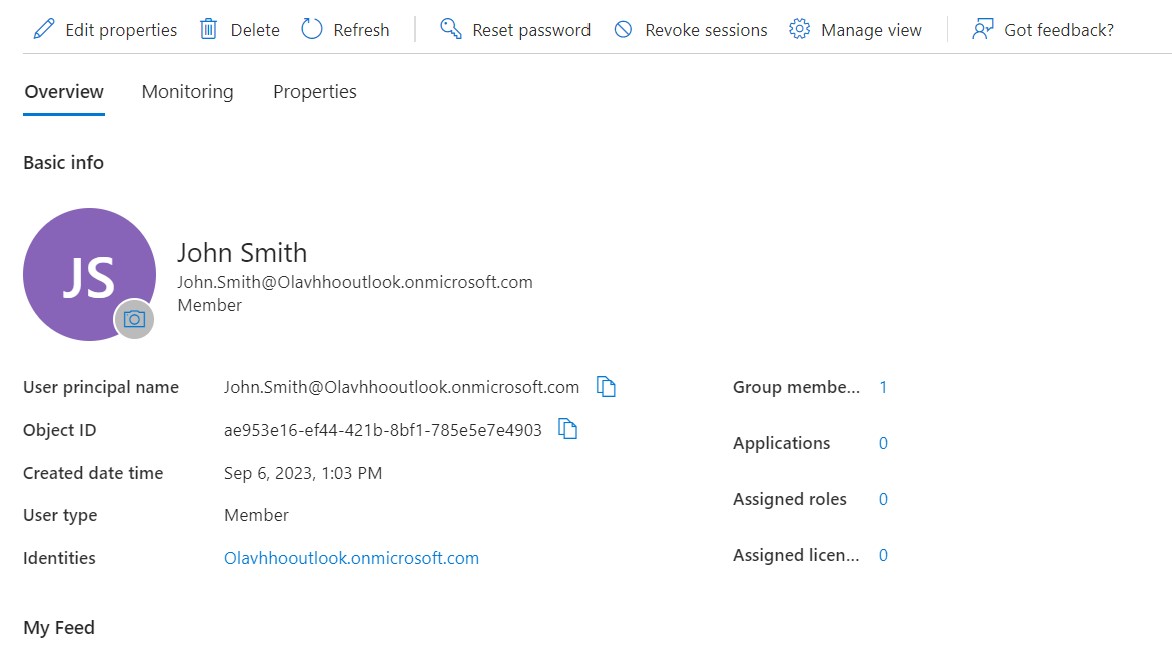
After triggering it for the last time, we can see that a user was created and he was assigned to the group Cloud Administrators. Logging in as the user we can see that he only has access to the resource group OnboardAutomator but not any other resource groups I have in my subscription. The Email action was also successful.
Conclusion
In doing this project I was able to get some hands on practice managing identities in Azure. Creating a user, creating groups and creating dynamic assignments (even though I could not use it). I also got some experience automating workflows in Azure, that was simple to start building with Azure Logic Apps.